The stub looks like this:
Sunday, December 27, 2009
How to Create your own Crypter stubs
Saturday, December 19, 2009
PRORAT - hacking continued
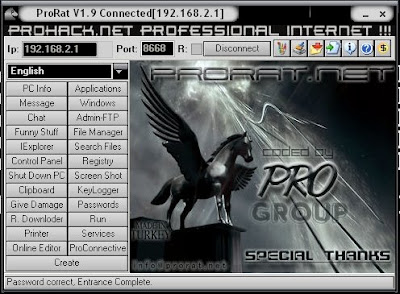
Hacking computer remotely - PRORAT:
Gmail hacking software
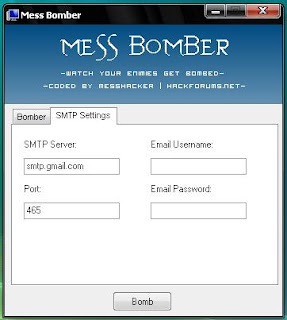
In my previous post i explained how to hack hotmail accounts today i will explain how to Hack gmail account
Gmail hacking software to hack gmail account :

Sunday, December 13, 2009
HOW TO FIND A IP ADDRESS OF A COMPUTER
Thursday, December 10, 2009
FUD CRYPTER : by pass anti virus detection
What is Crypter??
Wednesday, December 9, 2009
Hack administrator from Guest account.
today i am going to tell how to Hack administrator from Guest account.
Ever wanted to hack your college pc with guest account/student account so that you can download with full speed Hack Administrator !!!!there ? or just wanted to hack your friend’s pc to make him gawk when you tell your success story of hacking ? well,there is a great way of hacking an administrator account from a guest account by which you can reset the administrator password and getting all the privilages an administrator enjoys on windows..Interested ? read on…
Concept:
Press shift key 5 times and the sticky key dialog shows up.This works even at the logon screen. But If we replace the sethc.exe which is responsible for the sticky key dialog,with cmd.exe, and then call sethc.exe by pressing shift key 5 times at logon screen,we will get a command prompt with administrator privilages because no user has logged on. From there we can hack the administrator password,even from a guest account.
Prerequisites
Guest account with write access to system 32.
Here is how to do that -
* Go to C:/windows/system32
* Copy cmd.exe and paste it on desktop
* rename cmd.exe to sethc.exe
* Copy the new sethc.exe to system 32,when windows asks for overwriting the file,then click yes.
When asked to overwrite,overwrite the sethc.exe
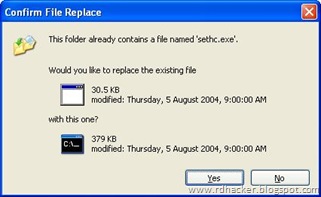
* Now Log out from your guest account and at the user select window,press shift key 5 times.
* Instead of Sticky Key confirmation dialog,command prompt with full administrator privileges will open.
* Now type “ NET USER ADMINISTRATOR aaa” where “aaa” can be any password you like and press enter.
* You will see “ The Command completed successfully” and then exit the command prompt and login into administrator with your new password.
* Congrats You have hacked admin from guest account.
Further..
Also, you can further create a new user at the command prompt by typing “NET USER john/ADD” where “john” is the username you would like to add with administrator privileges. Then hide your newly created admin account by -
Go to registry editor and navigate to this key
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList]
Here create a new DWORD value, write its name as the “user name” that u created for your admin account and live with your admin account forever :)
I hope that was informative..
Monday, December 7, 2009
ISTEALER :Hack email passwords
Istealer Password stealer - hack email passwords:
Sunday, December 6, 2009
DESKTOP PHISHING
Friday, November 27, 2009
PRORAT : Remote PC Access Software
remote pc access software.

Monday, November 23, 2009
Virus creator to create torjan virus
This virus creator software is easy to use and is used to create virus trojan which harasses user. In this article, I have explained how to create torjan virus
Virus creator to create virus trojan:
1. Download VIRUS CREATOR Software to create virus trojan.
2. Unzip the file using Winzix ( download here) to obtain Virus creator to
create virus
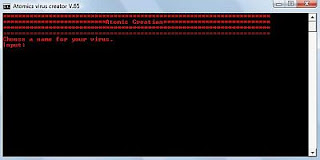
3. Run Virus Creator V.65 on your computer to get something like:
4. Now, Virus creator will ask you for various options listed below:
# name of virus
# Save virus to startup
# Save to homedrive
# Save to system32
# Save to desktop
# Disable scheduled tasks
# Create 10 users
# Corrupt system files
# Open 10 command windows
# Start world's most annoying webpages 10 times
# Reset time to midnight
# Memory leak
These options determine effectiveness of your virus. You can choose options preferences as you like and depending on amount of damage you wish the virus should do to victim.
Now, when you have selected preferences, simply press enter and virus creator software will create virus trojan for you.
5. Now, all you have to do is send this created virus to your victim and ask him to run this virus on his computer(Social Engineering). You can use Binder to make this virus undetectable from antivirus and even prevent doubt of victim.
You will require to have Winzix to download Virus creator software. Free Download Winzix here. Remember to install.
Thus, you now know how to create virus trojan using Virus creator software. Remember to bind this virus with Binder. I have tried to keep this virus creator tutorial simple. If you have any problem in usingvirus creator to create virus,please mention it in comments.
Enjoy Virus creator software to create virus...
Sunday, November 22, 2009
Binder software to disable Antivirus detection
What is Binder???
Binder is a free software used to bind or combine two or more files in one file under one name and extension. The files to be binded can have any extension or icon. The user has choice to select the name, icon and various attributes of binded file. If binded file contains an application (in our case - RAT or keylogger), the application is also run when the actual binded file is run.thus Binder is used to bypass antivirus detection.
I have provided link to download binder.
How to use Binder???
1. first of all, you need a binder. So, download free Binder software.
2. Unzip the downloaded file using Winzix (free download here) to obtain Binder setup.
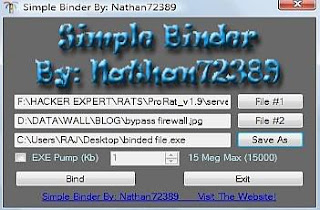
3. Install software on your computer to see:
4. Now, click on "Select File #1" and select the kelloger or RAT you wanna bind to avoid its antivirus detection.
5. Click on "Select File #2" and select the normal file with which you wanna bind our trojan, RAT or Kelogger.
6. Simply, hit on "Bind" to obtain the binded keylogger or trojan file. Now, simply send this file to victim whom this file will appear normal (trojan is hidden due to binding).
7. Remember to check both "Execute"options and you can use "EXE Pump" to increase your file size to desired value.
please post comments
Saturday, November 21, 2009
Use Mobile Phone as a Microphone and Speakers

No one like to use their microphone and speakers when they talk to their family and friend in Yahoo messenger, Msn Messenger, Skype, Google Talks and so many instant messenger software. Now you can make use of you mobile as microphone and speakers to talk with you friends and family believe me it's simple and easy, just follow the step by step guide and you will throw you microphone into bin forever.
You don't have to remain in one place to talk with friends an family, if you have USB bluetooth or WIFI router you can remain anywhere in your home and enjoy talking with your friends and save your cost forever.
Here is the step by step guide to make your mobile phone as microphone.
1. Download the file from This link and read the following steps.
2. In this file you will get one folder (I_LOVE_DVT) and two separate file. One is for PC application and another is for mobile application.
3. Install the PC software name as "mobiolaheadset2_wl_s60v3" in PC and install the mobile application name as "headset_s60_v_2_0" into mobile.
4. Remember if your don't have Blue tooth or WIFI functions, it will not work. Yeah it works for Cable but what is the difference between a cable and normal Microphone.
5. Installed the application in PC as well in mobile now open the folder "I_LOVE_DVT" and in it you will find two files, one is "keymaker" and other is "runme". Copy these two files into the install directory such as "C:\Program Files\Mobiola Headset for S60" and paste it.
6. Now run the "runme" and "keymaker" as well. From "runme" copy the Hardware fingerprint something like "373D-BCC0" into "keymaker's" H/W ID and press generate.
7. Now copy the keys and the name from "keymaker" into "runme" and press ok. It show valid. Now run the PC application and check it.
8. Than go to control Panel, sound and device. Run the sound and devices settings find the microphones one, select your microphone driver to mobiola and select the speaker driver.
9. Check your microphone by going to Volume controls and run any song to check your speakers that you can hear the song in your mobile speaker.
10. Enjoy talking with your friends and family and save your cost.
Friday, November 13, 2009
FOLDER LOCK -NO SOFTWARE
Labels: COMMAND PROMPT HACKING, HOW TO MAINTAIN A COMPUTER, TIPS AND TRICKS

Here is how to do that -
Create a new folder,rename it to a simple name like xero.
Now go to its properties,and choose a sprite less icon,which is next to a Yellow lock icon in third row.
Create a new text file in the same drive next to the folder and type thiscommand statement into it-
ren xero xero.{b5946137-7b9f-4925-af80-51abd60b20d5}
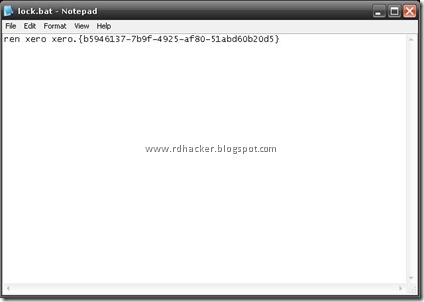
Now save this text file as lock.bat. Similarly create another text file and type this command statement into it-
ren xero.{b5946137-7b9f-4925-af80-51abd60b20d5} xero
Save this text file as lock.bat . Lock.bat will be used to make the folder inaccessible and Key.bat will be used to revert it into its original form.
What we have done here,is that we have renamed the folder with a random CLSID,which will change its identity into something else sing DOS. ‘CLSID’ is a unique registry-identifying component that is used to identify anActiveX control or in simple language,it identifies which file/control will be opened by which program in Windows. I have determined the CLSID by opening registry editor and searching for “CLSID” and choosing any random value like {b5946137-7b9f-4925-af80-51abd60b20d5} which I m using here.
Some common CLSID’s are -
- Recycle bin - 645FF040-5081-101B-9F08-00AA002F954E
- Control panel - 21EC2020-3AEA-1069-A2DD-08002B30309D
- Run - 2559A1F3-21D7-11D4-BDAF-00C04F60B9F0
- Search - 2559A1F0-21D7-11D4-BDAF-00C04F60B9F0
- Connect To - 7007ACC7-3202-11D1-AAD2-00805FC1270E
- Briefcase - 85BBD920-42A0-1069-A2E4-08002B30309D
- Help - 2559A1F1-21D7-11D4-BDAF-00C04F60B9F0
- Fonts - D20EA4E1-3957-11d2-A40B-0C5020524152
- Cameras and Scanners - E211B736-43FD-11D1-9EFB-0000F8757FCD
- My Network places - 208D2C60-3AEA-1069-A2D7-08002B30309D
Sorry for a little diversion,but I thought that was necessary. Now you have created the files,just double click the lock.bat file to make the folder inaccessible. Now the folder is invisible and also it cant be accessed by anyone.
But still,it has a name. So,in order to completely hide it, Rename it and enter an ASCII code by pressing ALT+0160 which will enter a null character in place of name and it will have No Name.
Congrats..Now you have created an inaccessible folder. To access it,just rename the folder into its original name and then click on key.bat . Now make sure to place the folder in a secure location and place lock.bat and key.bat in different locations . This simple folder lock is very effective as no one has idea that You can create it (sarcasm..again :P) .
Use some creativity and you can make that folder 100% inaccessible by encrypting it. I gave you a hint,find your own way :)
Hotmail Hacker - Hack Hotmail
Hotmail Hacker - Hack Hotmail password:
1. Free Download Hotmail hacker to hack hotmail password.
2. Download Winzix (free download here) to obtain Hotmail hacker folder.
3. Run, Hotmail hacker builder.exe file to see:
4. Now, enter your email account address, password and also the subject of email you want to receive. This email will contain the password you wanna hack. Also select appropriate smtp serveraddress. You can use smtp server addresses for this. Avoid use of hotmail email account. Can use gmail, yahoo or such. Click on "Build". This will create your own Hotmail hacker in Hotmail hacker folder.
5. Now, send this Hotmail Hacker.exe file to victim whose you wanna hack Hotmail password and tell him that this Hotmail hacker software is used to hack Hotmail password. Convince him that he can hack anyone's hotmail password using this Hotmail hacker. Ask him to run Hotmail Hacker.exe and enter all information (which includes his Hotmail id and password plus Hotmail id of victim he wanna hack).
6. As he enters this information and hits "Login And Start", he will receive error message as shown.
7. And you will receive in your inbox a mail like this:
8. Cheers.... you are able to hack Hotmail password using Hotmail hacker - hotmail cracker software.
You will require to have Winzix to get Hotmail Hacker software. Download Winzix here.
That's it for today. I hope you are now well approached with this way tohack Hotmail password using Hotmail hacker.This way to hack hotmail password using hotmail hacker is 100% working.. personally tested. If you face problems in using Hotmail hacker to hack hotmail password, mention it in comments.
Enjoy Hotmail hacker to hack hotmail password...




