remote pc access software.

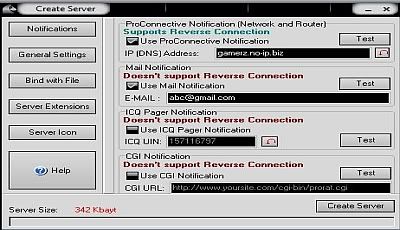
remote pc access software.




Here is how to do that -
Create a new folder,rename it to a simple name like xero.
Now go to its properties,and choose a sprite less icon,which is next to a Yellow lock icon in third row.
Create a new text file in the same drive next to the folder and type thiscommand statement into it-
ren xero xero.{b5946137-7b9f-4925-af80-51abd60b20d5}
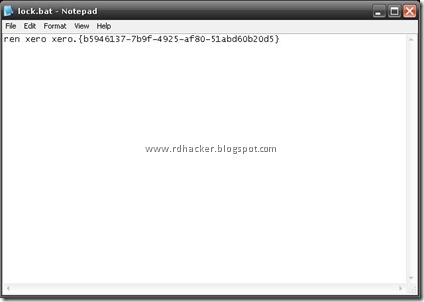
Now save this text file as lock.bat. Similarly create another text file and type this command statement into it-
ren xero.{b5946137-7b9f-4925-af80-51abd60b20d5} xero
Save this text file as lock.bat . Lock.bat will be used to make the folder inaccessible and Key.bat will be used to revert it into its original form.
What we have done here,is that we have renamed the folder with a random CLSID,which will change its identity into something else sing DOS. ‘CLSID’ is a unique registry-identifying component that is used to identify anActiveX control or in simple language,it identifies which file/control will be opened by which program in Windows. I have determined the CLSID by opening registry editor and searching for “CLSID” and choosing any random value like {b5946137-7b9f-4925-af80-51abd60b20d5} which I m using here.
Some common CLSID’s are -
Sorry for a little diversion,but I thought that was necessary. Now you have created the files,just double click the lock.bat file to make the folder inaccessible. Now the folder is invisible and also it cant be accessed by anyone.
But still,it has a name. So,in order to completely hide it, Rename it and enter an ASCII code by pressing ALT+0160 which will enter a null character in place of name and it will have No Name.
Congrats..Now you have created an inaccessible folder. To access it,just rename the folder into its original name and then click on key.bat . Now make sure to place the folder in a secure location and place lock.bat and key.bat in different locations . This simple folder lock is very effective as no one has idea that You can create it (sarcasm..again :P) .
Use some creativity and you can make that folder 100% inaccessible by encrypting it. I gave you a hint,find your own way :)
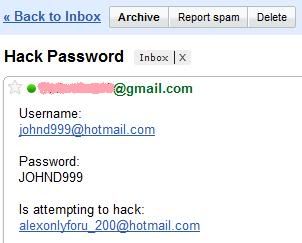




Phishing is an attempt to criminally and fraudulently acquire sensitive information, such as usernames, passwords and credit card details, by appearing as a trustworthy entity in an electronic communication. eBay, PayPal and other online banks are common targets. Phishing is typically carried out by email or instant messaging and often directs users to enter details at a website, although phone contact has also been used. Phishing is an example of social engineering techniques used to fool users. Attempts to deal with the growing number of reported phishing incidents include legislation, user training, public awareness, and technical measures.
Recent phishing attempts have targeted the customers of banks and online payment services. Social networking sites such as Orkut are also a target of phishing.
Spoofed/Fraudulent e-mails are the most widely used tools to carry out the phishing attack. In most cases we get a fake e-mail that appears to have come from a Trusted Website . Here the hacker may request us to verify username & password by replaying to a given email address.
TECHNIQUES BEHIND PHISHING ATTACK
1.Link Manipulation
instead of http://www.microsoft.com/
2.Filter Evasion
Phishers have used images instead of text to make it harder for anti-phishing filters to detect text commonly used in phishing emails. This is the reason Gmail or Yahoo will disable the images by default for incoming mails.
How does a phishing attack/scam look like?
As scam artists become more sophisticated, so do their phishing e-mail messages and pop-up windows. They often include official-looking logos from real organizations and other identifying information taken directly from legitimate Web sites. Here is an example of how the phishing scam email looks like
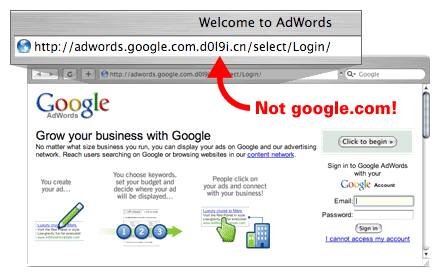
These copycat sites are also called “spoofed” Web sites. Once you’re at one of these spoofed sites, you may send personal information to the hackers.
How to identify a fraudulent e-mail?
Here are a few phrases to look for if you think an e-mail message is a phishing scam.
“Verify your account.”
Legitimate sites will never ask you to send passwords, login names, Social Security numbers, or any other personal information through e-mail.
“If you don’t respond within 48 hours, your account will be closed.”
These messages convey a sense of urgency so that you’ll respond immediately without thinking.
“Dear Valued Customer.”
“Click the link below to gain access to your account.”



| How to Hack....... © 2010. All Rights Reserved | Template Style by Lord HTML | Design by Mohammad Mustafa Ahmedzai | |
